
Shellmates club
blog

Log4J Vulnerability, all you need to know
Touami Mohammed - Binary Exploitation
Published on : 11/7/2022
Binary Exploitation
Log4j
Cybersecurity
Attack
Hacking
What is a vulnerability
Before looking at Log4j we first have to define what exactly is a vulnerability, in simple terms, a vulnerability is a weakness in a system that allows hackers to exploit it in order to deliver an attack, it can exist in a network, a hardware system, or in the case of Log4j, the software, more specifically a Java library.
Examples of common vulnerabilities
A vulnerability isn’t the attack itself or the threat to be attacked, it is rather the lowest point in a system from a security perspective, in other words a vulnerability is the mistake or misinterpretation made by the maker of the system regarding the security of its critical components (memory, routers, system files…). A critical component being easily accessible by non authorized users is the main risk here, we can think of an extreme case such as a company’s database being open to the general public (which obviously no company would allow), or a less risky case would be allowing your Bluetooth headphones to connect to any device without needing authentication.
The risk also extends to non critical components that might come into contact with the critical one; giving a programming library access to a section of your memory or a few registers might not seem as harmful at first since you wouldn’t expect a harmless library to suddenly attack your components, however, if the library falls into the hands of the wrong person, they might exploit it to alter these hardware components in a way that the library didn’t intend, which is actually what happened with Log4j.
What exactly is the Log4j library
Log4j is a Java based logging library made by Apache and written by Ceki Gülcü, the library is essentially used for logging system information during the execution of tasks, the library has multiple levels of logging for the user to choose from, they include: Off, Fatal, Error, Warn, Info, Debug and Trace. Each level offers an increasing amount of detail about the system’s condition, the instructions, the variables and the operating system.

Apache Log4j’s logo
The logged data can either be written into text form through log files (usually kept for higher log levels) or simply displayed on the status console. An option for custom log files is also available to allow the user to choose what kind of components and elements to track.
Log4j also allows personalized configurations using XML, YAML, JSON or the properties file format where the user can change the loggers, appenders, layouts and filters to provide an easier debugging experience for developers.
##How and when was the vulnerability discovered
In 2021, a security researcher working for Alibaba first discovered the vulnerability and reported it to Apache on November the 24th, and although it is unknown when exactly Log4j started getting used by malicious users, the first forensic investigations indicate the earliest use of it that they found was on the first of December of that year, however it might have been exploited way before that.
On the 9th of December Apache made the issue known to the public, which at first might look like the wrong move to make, but letting the developers that are implementing the library aware of its weakness was essential to do even though it comes with the cost of spreading the information to hackers that might consider jumping on it.
Funnily enough the vulnerability was first being used on the video game Minecraft, since it is programmed in Java, the discovery was announced on one of the video game’s forums where a user was able to send a remote code exploitation (RCE) over the game’s multiplayer servers and it worked.

Example of a Log4j RCE attack in Minecraft
How the vulnerability works
The vulnerability makes use of the logging library’s access to the system’s internal functions such as the directory services; this allows an attacker to send messages to Log4j that tell the system to download a malware from the server, this malware can either grant the attacker access to the system or work directly on sabotaging it.

Diagramme explaining how Log4j works
The attacker can make use of forms to insert the string that will download the malware, even a tiny name field in a log-in page can be exploited to enter the string, and if the server that receives this string uses the Log4j library, the string is logged into the console and depending on the way the console logs are handled, the string can launch the download of the malware directly.

Basic source code for launching a Log4j attack
The vulnerability actually went through multiple patches after its discovery, some of these were not able to fully fix the library’s weakness, it wasn’t until the 28th of December 2021 where patch 2.17.1 was released which finally gave a fix to the issue.
Who does it impact
Seeing as Java is one of the most used languages in the world, an enormous amount of systems was affected, with large companies at the top of the list. The library itself is also quite commonly used by these companies; after the announcement of the vulnerability to the public in December 2021, an incredible 10 million attempted attacks were recorded every hour by security researchers.

Number of attacks after Log4j announcement
The low difficulty of exploiting the library has invited low skill programmers to have a go themselves with these attacks. The main industries that were affected were those that handled large amounts of cash to run their business, the retail sector being at the top of the list with the Tech, financial services and manufacturing fields following closely.
Since the attacks are being directed at large scale enterprises, the ransomware that is implemented is going to work differently to the attacks targeted towards individuals; the goal of attackers here is to extract as much data from the target company as possible, this means that working with spyware is more favorable with destructive malware being a lower priority.

Explanation of using Log4j to breach a system
On an individual level there shouldn’t be too much worry, although there is still a small risk with certain smart home gadgets working with Log4j. Routers and network storage devices are also volatile, generally if you’re limiting your usage of these items to personal work you should be safe, however, if the attacker is really targeting you there is a chance that he is able to breach through and ruin your devices, since all it takes is the delivery of one string to the software of your device, so if you’re concerned about super sensitive information being volatile, make sure to contact the maker of these gadgets to question if they implemented the library and if there is a way to replace or update the item to a newer patch.
How was it fixed
A general rule of thumb to fix a vulnerability is to update to the latest version, and here it is no different, the patch 2.17.1 release in late December 2021 fixed most of Log4j’s weaknesses, however the risk still lies in the systems working with the library that are hard (or even impossible) to update. Even full on software systems that were updated are still threatened since it is unclear if previous attackers still have access to the system or not.
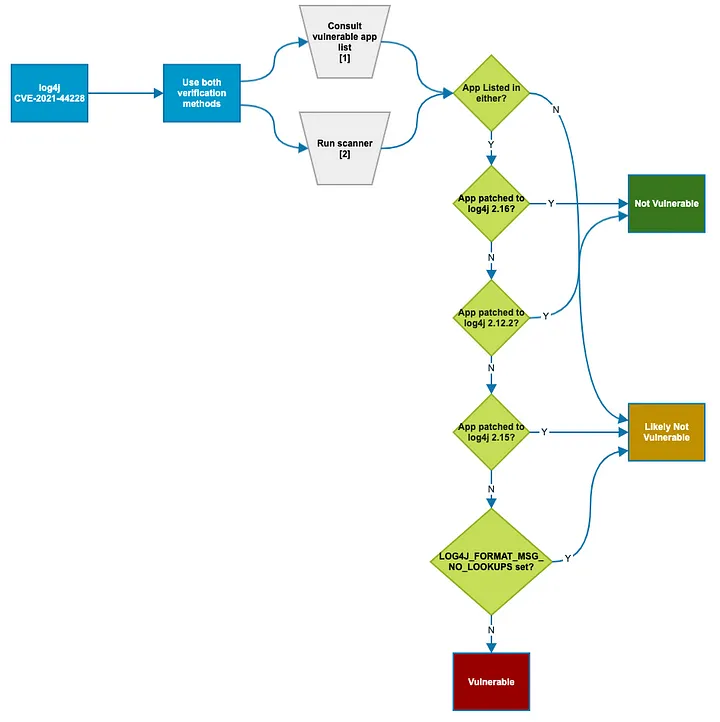
Guide from CISA on testing vulnerability of a system
An instruction manual from the Cybersecurity and Infrastructure Security Agency (CISA) provides advice on how to analyze internet-facing assets and prioritize updating. Additionally, it offers advice on how to keep an eye out for strange traffic patterns that can indicate attempts to exploit the Log4j vulnerability. As several of the earlier suggested indirect mitigation techniques have shown to be ineffective, this guideline also suggests that patching should be the primary and immediate focus. An updated list of these obsolete measures is kept by Apache.