
Shellmates club
blog
External network mapping (Gathering the departure points)
Aymen Benmalek - Cybersecurity
Published on : 7/16/2021
Cybersecurity
Hacking
Network
Web
Before we get started, we need to introduce some of the important terms that are often brought up when we are talking about penetration testing or bug bounty:
- External attack surface:
The set of different points from which an attacker can enter the system to access data or launch an attack. It consists of the assets of the company that are visible by external parties on the internet. These assets are generally linked with each other, and with the rest of the system. Which makes it important to identify and test them against security vulnerabilities. There are different components that go into the external attack surface namely: website, Domain name servers (DNS), web servers, IP addresses, Autonomous System Numbers (ASNs), etc.
- ASN numbers:
Autonomous systems or ASs are wide area networks, consisting of one or more IP prefixes (network identifier), that share a well-defined routing policy and that are generally controlled by a single organization. The Autonomous system Numbers (ASNs) are 16-bit numbers between 1- 65534 or 32-bit numbers between 131072–4294967294 that uniquely identify the autonomous system of an organization and allows it to share its routing information with other systems.
- Target scope:
A target scope defines the elements of the system that the tests are allowed to be operated on, and those that are excluded. In other words, the scope defines the boundaries. The tester is allowed to attack anything within the scope following well defined rules, and everything else that is not included in the scope is off limits.
- Warming up:
Sometimes it happens that a company allows a pentester or a bug bounty hunter to target any external surface that belongs to it, we can take Verizon Media, Tesla Motors as an example, in those cases the if you try to apply the classical methods such enumerating the main app subdomains ip’s etc … most likely you’ll be missing a bigger part of their external surface. The point from this article is to provide the reader with a general idea about dealing with a large scope company that is involved in more than a business and has lots of acquisitions.
Introduction :
As mentioned before the point from the article is to map the external network of a particular target. Speaking of process, it can be really passive since we have to get several external attack surfaces that can be different seeds/root domains or IP ranges that we will enumerate them in our active recon steps without even touching the target itself.
Acquisitions :
Acquisitions are companies that are acquired by our target and most of the time they are a part of the target’s scope (speaking of wide scope targets)
Why acquisitions : they are likely to be more vulnerable than the target core apps for several reasons, just think about who developed and deployed those apps in the first place and if he really cared about security during the development cycle of the apps.
Wikipedia and Crunchbase come to your rescue whenever you want to know about a company’s acquisitions.
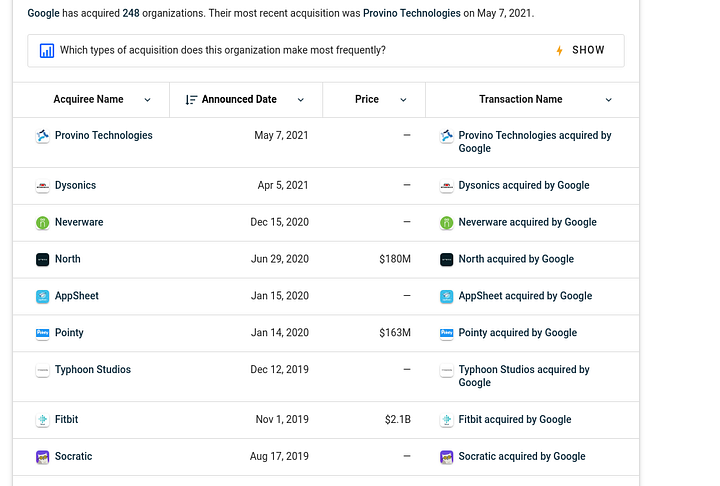
As illustrated in the screenshot, all you have to do is visit a company page in Crunchbase then you can scroll through their acquisitions.
Personally I prefer crunchbase.com, the reason is that wikipedia is not maintained and the information there can be out of date in contrast Crunchbase is more trusted at least from my own perspective, but as you know google is your friend it’ll be better if google information about an acquisitions by yourself.
ASN enumeration :
We have already introduced you to what is an ASN, so let’s get to the technical side
How an ASN number can be helpful for mapping an external attack surface :
Not only ISPs have ASN numbers but also large network companies. Theoretically we can get the ASN number of a particular company through a domain or an IP address that we already know but generally we are going to use some existing tools or websites such as Amass or https://bgp.he.net, but for now the important question is what are we going to get from the ASN numbers, basically we will get the IP pool of a company and if the PTR record is configured in the DNS configuration we can resolve those IPs to domains, also running ports and vulnerability scans on those IPs is an option, I can’t talk about port scans without mentioning brutespray basically the tool is meant to take an nmap scan output and targets the remote administration protocols for default or weak passwords (you can imagine an easy remote access can be achieved with low efforts). But since the article scope is about mapping the external network of a target we are going to introduce only how to get useful information from ASN numbers without taking a deep dive into active recon techniques.
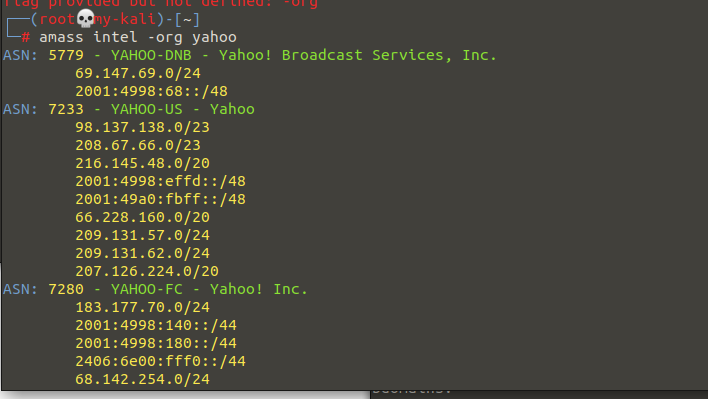
This is an example of the use of amass to get ASN numbers of a particular company, just by typing the command amass intel -org <company_name> you’ll get the asn numbers of the company and the cool thing is that Amass used to display only asn numbers but now as illustrated in the screenshot it displays more information about the IP pool of a company in both IPv4 and v6, but for now just keep in mind the ASN numbers such as YAHOO-DNB ( ASN : 5779 ). In fact using CLI tools such as Amass can lead to some kind of false positives since they can return a record that belongs to another company just for the reason that it contains a keyword that refers to our target ( it can be Yahoo, Tesla or anything similar to our target name ), we can solve this problem by the use of https://bgp.he.net .
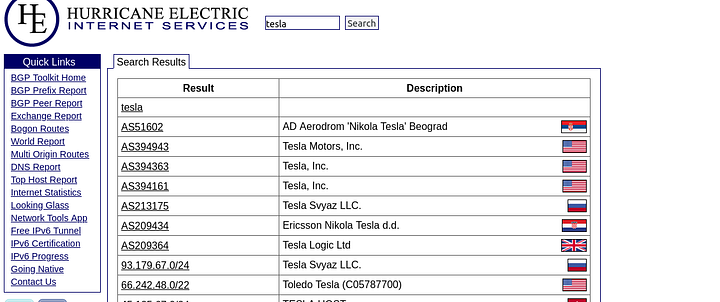
The information here is more accurate. Now that we have got the ASN numbers we can get the IP pool through Nmap or a simple bash one liner, personally I use the bash one liner since I’ve the ability to customize and play with the input/output whenever I wish to.
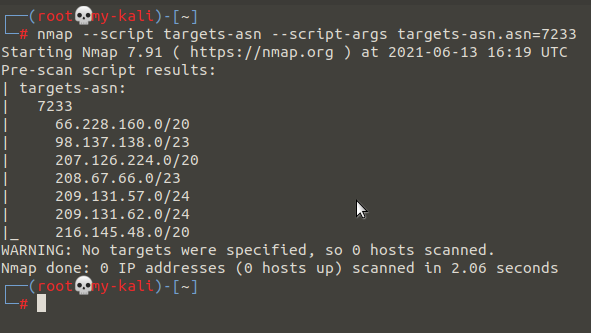
As shown in the screenshot this is an Nmap script that takes the ASN number as an input in the targets-asn.asn=<ASN_NUMBER> and returns the IP ranges that belong to that ASN number.
As a reminder we have to take notes of those IP ranges and ASN numbers and if you don’t want to waste time you can just use the Amass output but make sure that you compare the Amass returned ASN numbers with the ones that are mentioned in https://bgp.he.net otherwise you may accidentally launch your vulnerability testing against another company and not your target.
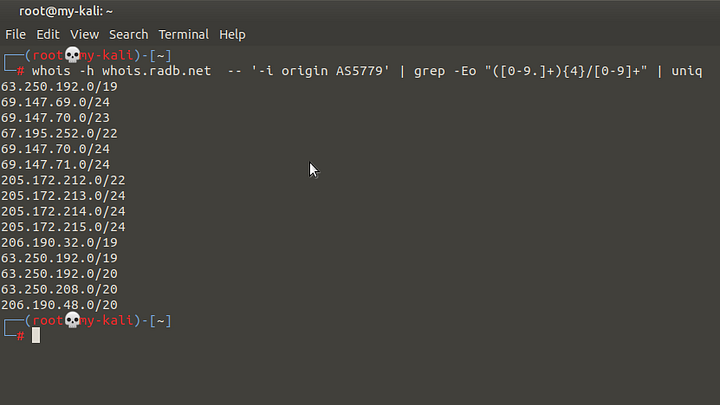
Personally as I mentioned before I use this bash one liner for a simple reason that I can loop over the asn number value. Basically this bash one liner uses whois to query whois.radb.net for IP ranges that belong to a particular ASN number, the regex is used to grep only ip ranges from the returned data and the uniq command is supposed to remove duplicated ranges.
Now that we have got the IP pool of our target we can use it for multiple things but for now the most important thing is to get root domains through those ranges, we can use host or dig commands to loop over those ranges looking for resolvable ones, but personally I use Amass for this step, it basically takes an ASN number and returns the root domains that belongs to it.
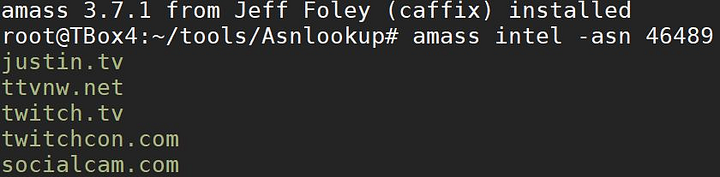
As you can see in the screenshot above, the provided ASN belongs to Twitch and through the command amass intel -asn <ASN_NUMBER> we can get the root domains that belong to that asn number. This process consumes lots of resources so it’s a normal thing that you’ll experience some kind of networking problems.
What have we got until now :
Until now we have got the acquisitions names which we can get their core app domains with a simple google search ( taking notes of them is really helpful ), we have also got both ASN numbers and the IP pool of the company which we can use them during our active recon steps ( port scans, vulnerability scans, brute spraying etc … ), we have also got root domains from the ASN numbers of our target. We have to take notes of them to enumerate them in later steps.
Google Fu :
Maybe most of you are already familiar with Google dorks/hacking but for those who are not google hacking, dorks or google fu are expressions to refer to some keywords that we can use with google’s search engine to narrow down our search results. For example if we are looking for a pdf then there’s no point from scrolling through multiple results that are not pdfs. In this case we can use the ext: keyword that represents the file extensions ( ext:pdf ). Due to the use of the ext: keyword google will return results that are limited to the pdf files.
Now let’s explain what are the benefits of the use of google dorking. Let’s say that our target login pages or any random pages have common expressions even in different subdomains or domains ( most commonly copyrights ). As an example this is logitech, a company that has a public bug bounty program on Hackerone, we can see a copyright sign at the bottom of their main web page.
Let’s try to google-fu that expression with something like intext:"©2021 Logitech. All rights reserved". The keyword intext instructs google’s search engine to return any page that has the specified expression within its lines. Here’s a sample of the returned data.
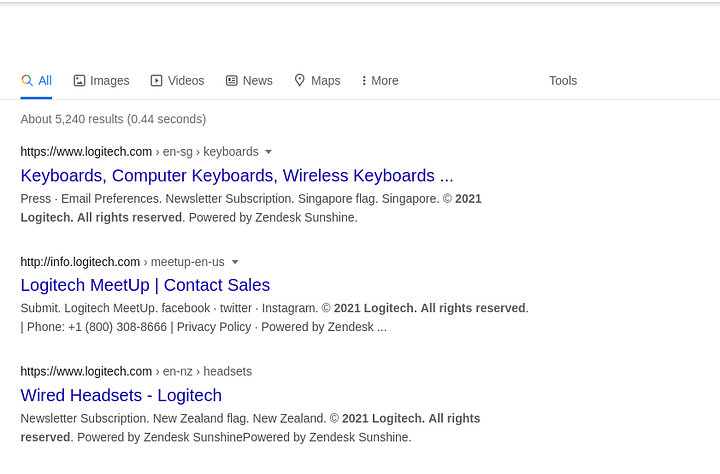
Speaking facts I personally don’t use this technique; more particularly I’ve never used it before. Why ? well it takes lots of time and most likely the domains that you’re going to gather are already gathered during the ASN recon step. So what I do is to keep an eye on any page that has some CVE’s or a particular vulnerability ( if it contains any keywords that seem to exist elsewhere on the internet ) then I google them up. I know what I’ve mentioned has nothing to do with recon but I found it worthy anyways.
For transparency I am not saying that google-fu is not worth it but I personally believe that is more worthy when it comes to dumpster diving or other kinds of recon not generally mapping an external network.
Ad/Analytics Relationships :
Recently I started to look for analytics and Ad relationships, it’s a simple technique that allows us to find sub/domains that share the same ad or analytics technologies ( they may be false positives ). Sometimes even false positives are helpful just imagine finding a website that belongs to a developer who developed or contributed in the development of one of our target websites, in such cases most likely I am looking for the developer github account, pastebin or anywhere on the internet where it’s possible that the developer has leaked some data/tokens that belongs to our target.
https://builtwith.com/relationships/< target > is our handy tool in this topic, it allows us to scroll over the similarities between our target and other hosted websites. Here’s a sample of what BuiltWith might return.
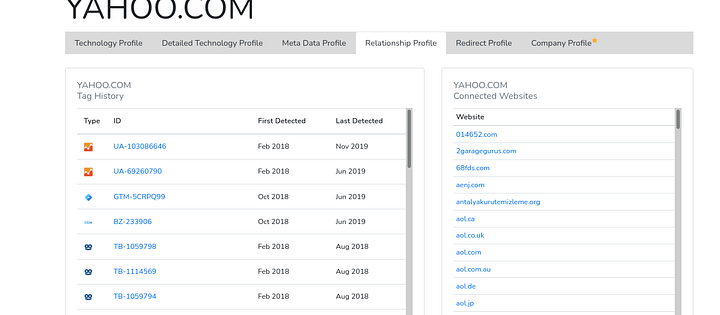
Without taking a deep dive into the results looking for yahoo ad and analytics relationships is going to end up with many domains that belong to the parent company which is Verizon Media and this is the point that I wanted to show which is the ability to find acquisitions through this technique.
Conclusion :
Recon has always been the most critical step of a red team, pentest or any type of offensive engagements. What we have done until now is that we were able to determine just where the departure point is and what it looks like. But in fact there’s more to be done, each time you find a deep level subdomain you have a bigger chance to find a vulnerability, and this is exactly what we’re planning to talk about in the next article.